T2 interfacing AI and standard monitoring tools
The following screenshots illustrate a small overview of Tranalyzer output and its application in practice. Tranalyzer is capable to run in several modes concurrently, such as flow, packet, monitoring, alarm, force, data carving and logs into well established NetFlow tools such as nfcapd. Moreover practical features are provided for traffic mining, troubleshooting and geolocation-whois purposes.
End report
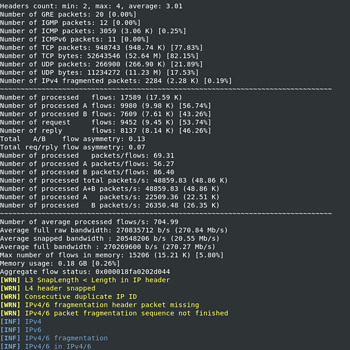
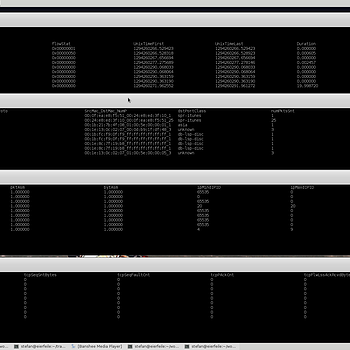
Rapid traffic assessment
T2 end report enables the user to rapidly assess the significance of large pcaps without even looking into the flows.
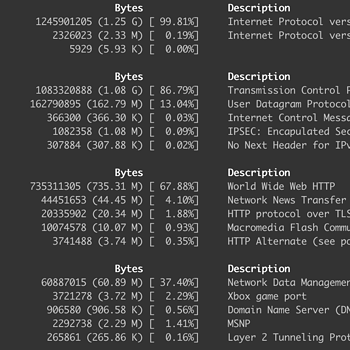
Protocol aggregated summaries
Layer 2/3/4 statistics
Specialized statistics files, such as Layer 2/3/4 protocol statistics, are generated to assess protocol anomalies before even looking into flows.
Protocol aggregated summaries
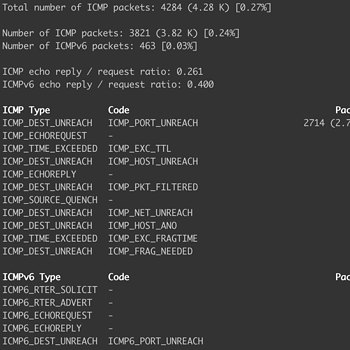
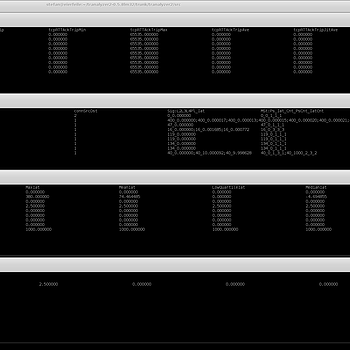
ICMP anomalies
If you know and manage your network, the ICMP summary file reveals traffic anomalies useful for troubleshooting and security.
Packet size inter-arrival time statistics
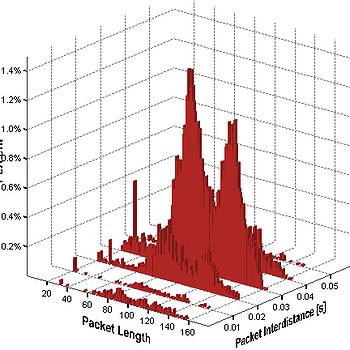
Encrypted traffic mining statistics support
Preprocessing for statistical traffic mining in encrypted voice communication, e.g. Skype, using pktSIATHisto plugin: packet size inter-arrival time distribution per flow. Also useful for multimedia developers who want to protect their application from mining attacks.
Monitoring
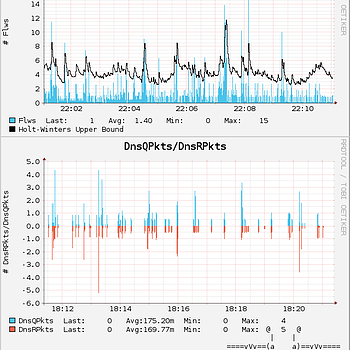
RRDtool
T2 in monitoring mode piped into t2rrd which feeds RRDtool.
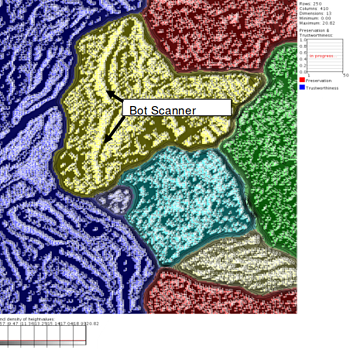
(Un)supervised learning support
ESOM
AI based traffic mining using the 11 dimensional vectors of T2's descriptiveStats plugin. Our ESOM (Kohonen Network) classifies traffic and detects abnormal traffic, such as bot networks, automatically.
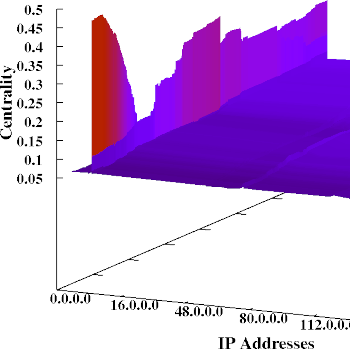
Flow graph
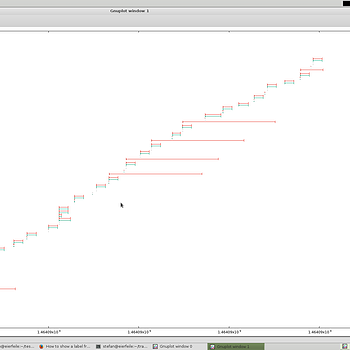
Rapid traffic flow anomaly detection
The script t2timeline produces flow graphs. Among other applications, they also help to assess the proper generation of training data. Both plots above should look alike, but do not... Somebody messed up the traffic production!
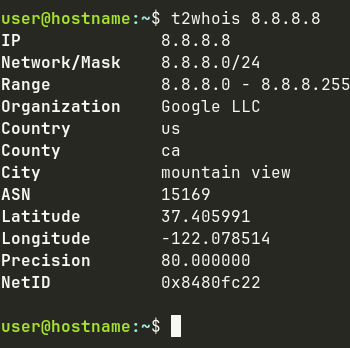
t2whois organization & geolocation
Geolocation, whois
The Anteater supplies t2whois, a local Whois and Tor service for geolocation.
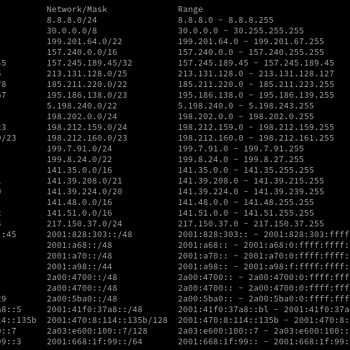
t2whois geolocation server
Geolocation, whois, tor
t2whois functions also as a local geolocation and Whois server also labeling Tor exit, guard and directory nodes.
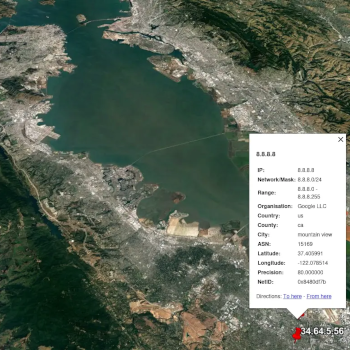
t2whois IP address mapping
IP mapping
Visual address mapping onto Google Maps.
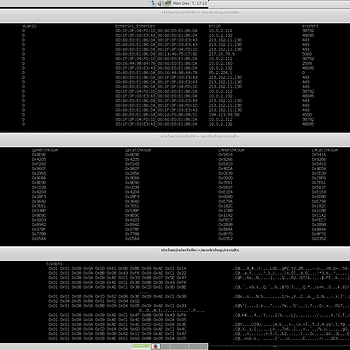
Flow view standard plugins
Flow output
The flexible flow aggregation scheme of T2 is dependent on the plugins being loaded and their configuration. In contrast to other tools, e.g., Bro/Zeek, it is AI friendly, mining compatible and directly exportable into tools such as SPSS, Excel, Rapid Miner or post processed via command line. Special anomaly flag enable efficient drill down to data carving.
Flow view protocol plugins
Higher protocol plugins
L4/7 protocol plugins for specific troubleshooting, mining or anomaly detection. Several post processing scripts are provided to facilitate the analysis job for practitioners and researchers.
Packet view
Command line friendly tshark
As a complement to TShark/Wireshark, T2 provides a performant command line and mining friendly packet mode which allows an easy correlation with flow and content data.
A day in the Anteaters life
Here are several spontaneous shots revealing the secrets of the Anteater's performance.
Sniffing the network
Sometimes he spaces out in the server room and sniffs traffic to train his anomaly detection and monitoring capabilities.
Keeping the big picture
Andy sometimes elevates himself to get the big picture, inspiring new ideas for the T2 end report
Keeping sharp in traffic mining
Reading research papers and communicating with universities Andy always sharpens his Encrypted Traffic Mining skills on real world packets.